All 24
All 24 /Blog 23 /Business Continuity and Disaster Recovery 0 /Cloud 0 /Communications 0 /Cybersecurity 12 /Data Management 0 /eBooks 0 /infographic 0 /IT Best Practices 0 /IT Consultant 0 /IT Risk Management 0 /Main Pages 0 /Managed Services 0 /Network Monitoring & Testing 0 /Networks 0 /Penetration Testing 0 /Security Maturity Level 0 /Solution Landing Pages 0 /Uncategorized 0 /vCISO as a Service 0 /VoIP 0 /White Papers 0

How to Beef Up Your Incident Response Plan
Are you prepared to face a cybersecurity breach, a natural…
April 5, 2024/by Sherry Haney
Don’t Make These Incident Response Planning Mistakes
Worried about cyberattacks hitting your business? You're…
April 5, 2024/by Sherry Haney
Checklist: Is Your Business Breach-Ready? Find Out With Our Free Checklist
Assess Your Cybersecurity Preparedness and Learn How to…
April 5, 2024/by Sherry Haney
Infographic: Fortify Your Business Against Cyberattacks in Four Simple Steps
Download our infographic to build an effective & resilient…
April 5, 2024/by Sherry Haney
The Hidden Costs of Ineffective Data Management
In today's business landscape, data isn't just power…
March 5, 2024/by Sherry Haney
A Deep Dive Into Data Governance
In the world of business, your data holds the key to…
March 5, 2024/by Sherry Haney
Infographic: Fuel Business Growth by Unleashing the True Power of Data
Download our free eBook to transform your data into a strategic…
March 5, 2024/by Sherry Haney
Checklist: Empower Your Business With Proactive Steps to Protect Data
Download our free checklist to fortify your cyber defenses
UData…
March 5, 2024/by Sherry HaneyUData…

Bolster Cyber Defenses With Routine Security Tests
Businesses today face a range of cybersecurity threats,…
February 5, 2024/by Sherry Haney
Tackling the Hidden Challenges of Network Monitoring
Your network is your business’s lifeline.
A healthy…
February 5, 2024/by Sherry HaneyA healthy…

Checklist: Is Your Network Hiding an Illness? Take the Free Network Wellness Check
Download our free checklist to keep your network in top…
February 5, 2024/by Sherry Haney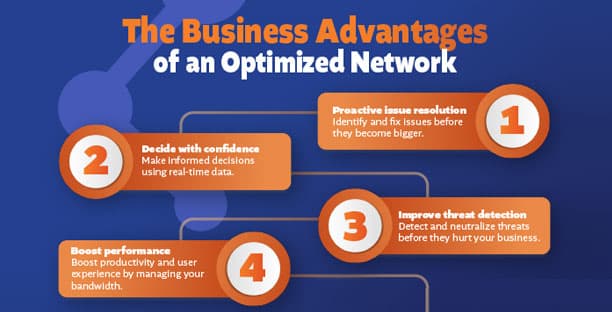
Infographic: Unlock the Business Advantages of an Optimized Network
Download our infographic to achieve improved network…
February 5, 2024/by Sherry Haney
How to Ensure Your Cyber Insurance Pays Out
In the current digital environment, where cyberthreats…
December 29, 2023/by Sherry Haney
Key Considerations When Selecting the Right Cyber Insurance Coverage
Is your business prepared to confront today’s growing…
December 29, 2023/by Sherry Haney
Infographic: Protect Your Business From Cyber Insurance Claim Denials With Our FREE Infographic
Download our infographic to learn how to maximize your…
December 29, 2023/by Sherry Haney
Checklist: Uncover the Secrets to Securing the Right Cyber Insurance
Protect your business wisely with informed cyber insurance…
December 29, 2023/by Sherry Haney
How Effectively Managing Risk Bolsters Cyber Defenses
In today’s rapidly evolving digital landscape, where…
December 1, 2023/by Sherry Haney
How to Achieve Strategic Cyber Risk Management With NIST CSF
Keeping sensitive data and critical tech safe from cyberattacks…
December 1, 2023/by Sherry Haney
Checklist: Cybersecurity Risk Management Made Easy
Get your free checklist and identify threats that can…
December 1, 2023/by Sherry Haney
Infographic: Assess Your Cybersecurity Risks in 7 Steps
Technology Budgeting
Boost your cyber defenses with our…
December 1, 2023/by Sherry HaneyBoost your cyber defenses with our…

Top Misconceptions About Digital Transformation
Digital transformation is necessary for all businesses…
November 2, 2023/by Sherry Haney
Top Technologies Driving Digital Transformation
When creating a budget for your business, it’s important…
November 2, 2023/by Sherry Haney
Checklist: Achieve Digital Transformation With Our Checklist
Unlock the power of digital transformation for your business.
If…
November 2, 2023/by Sherry HaneyIf…

Infographic: Drive Business Success Through Digital Transformation
Technology Budgeting
Download our infographic to harness…
November 2, 2023/by Sherry HaneyDownload our infographic to harness…

